Securing Data in Salesforce Marketing Cloud – Part Three of Three
Introduction
Welcome to the final installment of “Securing Data In Salesforce Marketing Cloud!” This informative article is part three of a three-part series created by one of Devs United’s knowledgeable Technical Architects.
Part Three covers the advantages and considerations of the following security features in Marketing Cloud:
- Field-Level Encryption
- Transparent Data Encryption
- Shield Platform Encryption
Go to Part One | Go to Part Two
Field-Level Encryption
The Marketing Cloud permits encryption of data at field level. This product encrypts data at rest to facilitate compliance with corporate privacy policies, regulatory requirements, and contractual obligations for handling private data. The system converts encrypted fields to plain text at the time of send.
How Field-Level Encryption Works
The Marketing Cloud encrypts sensitive data using a cryptographic symmetric key generated via Encryption Key Management. You must provide both a key value and an initialization vector (IV) when using encryption keys. This feature also permits importing encrypted data into the Marketing Cloud. In this case, you must still provide a key value and IV via Encryption Key Management for decryption at send time.
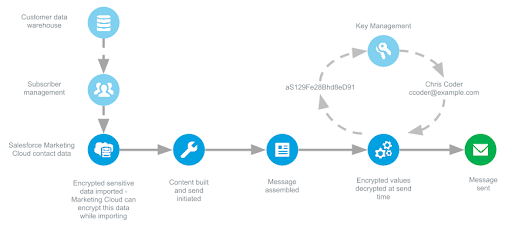
Once you choose your encryption method, create data extensions using the Contact Builder application within the Marketing Cloud to contain the encrypted data. Data extensions can store encrypted text or email address data. You cannot select fields to encrypt when creating data extensions from within the Email application in the Marketing Cloud. You can only encrypt data using data extension created through Contact Builder.
You cannot share encrypted data or key values across business units.
You may also input data directly into the data extension by adding individual records. This method encrypts data as well.
The Marketing Cloud builds a message using encrypted data, then converts that data to plain text using a symmetric key at send time. The system then sends the message from our mail transfer agent (MTA). The Marketing Cloud stores all tracking and deliverability information as identified by the corresponding subscriber key values.
Encryption Configuration Options
Choose one of these options when enabling Field-Level Encryption for your account:
- You encrypt your data and import it into your Marketing Cloud account. Any extracted or exported data remains encrypted.
- You import plain text data into your Marketing Cloud account, which encrypts that data as part of the import process. The Marketing Cloud then decrypts any extracted or exported data. The Marketing Cloud exports any data using a data extension export to an FTP location as unencrypted data. You can use PGP encryption on data imported using SFTP as files.
- You choose to display data in Preview, landing pages, View as Webpage, Forward to a Friend, platform apps, and Send Logging in unencrypted text. By default, the Marketing Cloud encrypts this data.
Advantages:
- With Field-Level Encryption turned on, import data into the Marketing Cloud using one of these methods:
- Imports
- API Call (CreateRow, UpdateRow)
- Triggered Send
- Data Extension AMPscript Functions (Lookup, InsertDE, UpsertDE)
- With Field-Level Encryption turned on, export data from the Marketing Cloud using one of these methods:
- FTP export of a data extension from Contact Builder
- File download of a data extension via browser from Contact Builder
- Extract via Interactions – this method exports data as encrypted data only
- API retrieval of a data extension
Considerations:
- Only new accounts can use Field-Level Encryption.
- Field-Level Encryption requires encryption of any email address fields used for sending.
- Field-Level Encryption requires a subscriber key for each contact.
- All business units within an Enterprise account must use Field-Level Encryption. You cannot turn on Field-Level Encryption for one business unit within an Enterprise account.
- Field-Level Encryption does not support segmentation, filtering, or querying of encrypted fields.
- Discover and standard reports show encrypted data as still encrypted.
- Field-Level Encryption does not support auto-suppression lists.
- You cannot add or update encrypted data via the Marketing Cloud app. You must use imports, AMPscript, triggered sends, API calls, or manually adding records into a data extension using Contact Builder.
- Field-Level Encryption does not support encryption of a mobile number used as a subscriber key value.
- You cannot turn off Field-Level Encryption once you enable it.
- You must use the same encryption keys across an enterprise.
- Field-Level Encryption does not support list-based sending.
- Accounts enabled for Field-Level Encryption do not support data filters. Use query activities instead.
Transparent Data Encryption
TDE encrypts the underlying files stored in the database. TDE encrypts data at rest using SQL Server’s built-in data protection technology.
Advantages:
- TDE presents data to the Marketing Cloud application as plain text while encrypting the underlying filesystem. TDE does not utilize application-layer or field-level encryption.
- TDE allows you to implement encryption without modifying existing application code.
- The encryption uses a database encryption key (DEK) stored in the database boot record for availability during recovery.
- The DEK uses one of these key values:
- Symmetric key secured by using a certificate stored in the master database of the server
- Asymmetric key protected by a Hardware Security Module (HSM), or in some cases in an encrypted database
Considerations:
- Existing customers on a multi-tenant database require a service engagement to enable Transparent Data Encryption (TDE).
- TDE performs real-time I/O encryption and decryption of the data and log files. This process incurs some performance overhead, due to encryption and decryption processes.
- TDE within the Marketing Cloud environment requires a dedicated database. Existing customers on a multi-tenant database need to migrate to a single-tenant database to implement TDE.
- TDE applies only to data residing in the SQL Server.
- The following features store data in other locations, preventing TDE from implementing encryption for that data:
- Predictive Intelligence
- Audience Builder
- Social Studio
Shield Platform Encryption: an option to improve our security
Shield Platform Encryption gives your data a whole new layer of security while preserving critical platform functionality. It enables you to encrypt sensitive data at rest, and not just when transmitted over a network, so your company can confidently comply with privacy policies, regulatory requirements, and contractual obligations for handling private data.
Shield Platform Encryption builds on the data encryption options that Salesforce offers out of the box. Data stored in many standard and custom fields and in files and attachments is encrypted using an advanced HSM-based key derivation system, so it is protected even when other lines of defense have been compromised.
Your data encryption key is never saved or shared across organizations. Instead, it is derived on demand from a master secret and your organization-specific tenant secret, and cached on an application server.
Conclusion
Salesforce Marketing Cloud with the classic encryption tools provides the mechanisms to ensure the access, storage and reuse of data within Marketing Cloud as well as other services provided by Salesforce.
We will have to consider certain restrictions when analyzing what type of security our organization requires, which will be solved by adding or activating a feature or functionality.
If you need an additional layer of security you can purchase the Shield Platform Encryption add-on which will not only give you more flexibility but also comply with private data regulations and obligations.
The “Securing Data in Salesforce Marketing Cloud” complete article is available for download here in PDF format.
